PSYCH! Home Page:
PSYCH! Process Page:
PSYCH! Final Live Stream Page:
IN THE END…….
Reflections:
General Learning Points:
Live streaming is really very spontaneous and requires quick thinking and reaction in real time. It exhibits the realness of the situation with the setup and props making it more believable. Audiences are made unintentional voyeurs when they indirectly spy on Clarita’s Facebook information as well as Ling Ern’s camera.
We gave the audience a sense of autonomy when they can contribute to the collect narrative and their decisions make an impact on the live stream. These greatly increase the level of relatedness and involvement of their participation.
However, live streaming also meant that it provides little room for mistakes as these actions cannot be unseen by our viewers. When we faced technical difficulties, we must find ways to react quickly to our live audience.
LING ERN POV:
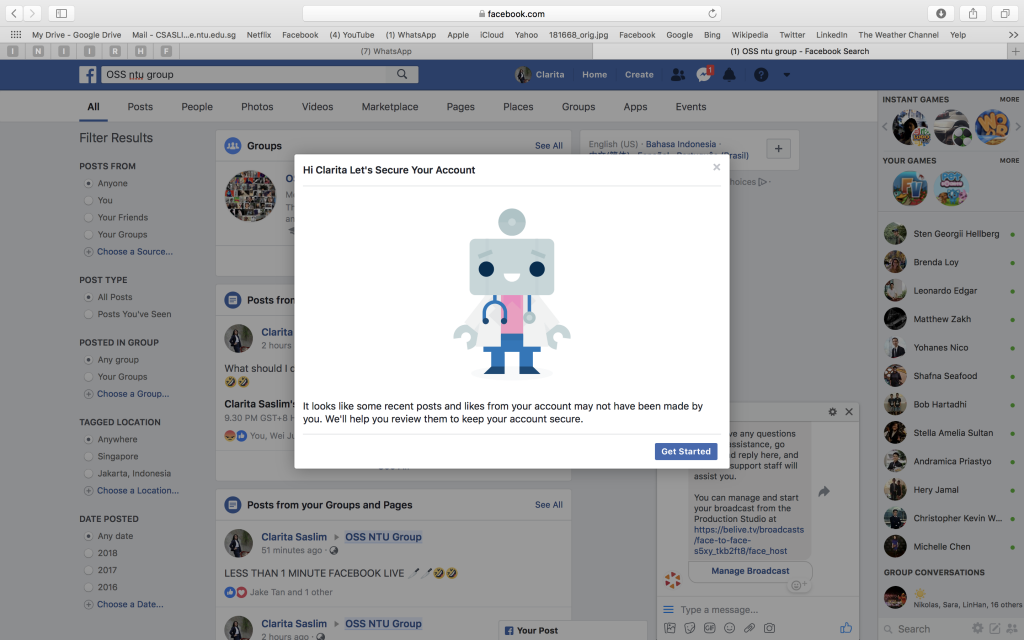
Through playing the role of a victim, I realised the vulnerability of online users and how our traces left behind to serve as baits for hackers to target us. The consequences can be very devastating for the victim and it truly invokes audiences to rethink their own actions. For instance, not clearing your cache or browser history after doing a bank transaction or avoid using Free Public Wifi often as we are unaware of the origin of the service provided. All these can easily lead to data breaches and theft of confidential information, especially after the talk by Surya Mattu about the WIFI Packet Sniffer.
The devastating consequences in this short role play caution our online audience to take the initiative to protect themselves over the internet, such as reading small print terms and conditions before agreeing to an app that may collect your personal information. We can deny app permissions to access our camera and microphone instead of clicking “ok” right away each time we download a new app. Similar to my reaction in the video when victims are flustered, we do not think rationally and provides our information right away to the other party.
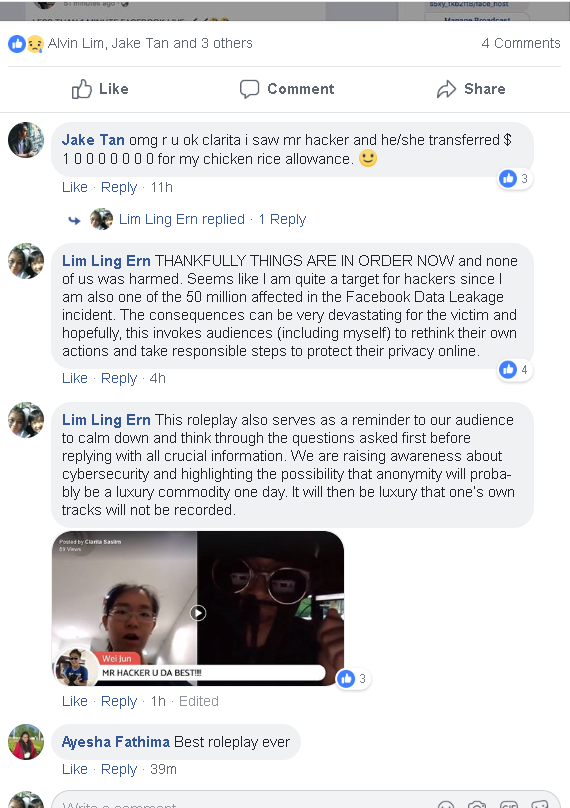
This roleplay also serves as a reminder to our audience to calm down and think through the questions asked first before replying. We can raise awareness about cybersecurity and highlight the possibility that anonymity will probably be a luxury commodity one day. It will be luxury that one’s own tracks will not be recorded.
CLARITA POV:
By putting ourselves into the position of a hacker. We explored the motivation and intention of the hacker and realised how anonymity can encourage people to be bolder in terms of unethical behaviours, especially for monetary gains and voyeurism. The availability and high accessibility of applications in which anonymous people can use to change their identity, for instance, the voice changing app and IP changer hacking code.
Similar to what Sarah Watson mentioned about how we leave traces on the internet very easily making us highly trackable, these are the kind of loopholes that allow hackers to make use of people’s data and further breach their privacy and take advantage of their personal information. These hackers can then get away easily with the anonymity which explains the increasing number of phone calls we receive nowadays impersonating the police saying that “We have your package at the customs and hence we need your personal information to approve it” or impersonating a company personnel stating that “Congratulations you have won yourself a grand prize and you need to pay this handling fee before getting your item.”